Products: Managed Backup (Agent), Managed Backup (Web)
Article ID: m0696Last Modified: 13-Nov-2025
Prepare Microsoft Entra ID Account
To start using lifecycle policies for Microsoft Azure Blob storage accounts, you need an Microsoft Entra ID user account.
- Go to the Azure Portal.
- Click on Microsoft Entra ID.
- Click on Users
- You can either create an entirely new user account or use the User principal name of an existing account to create an administrator account in Management Console and then log in to Management Console with your Microsoft credentials.
Create New User on Azure Portal
- Go to the Azure Portal.
- Click on Microsoft Entra ID.

- Click on Users
- Click + New user and select one of the available options. This article describes the Create New User option.
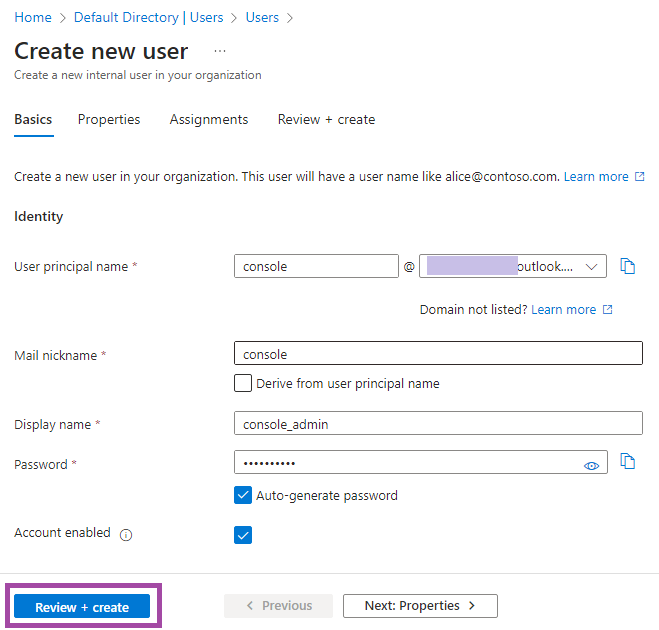
- Enter the required information and click Review + create.
- Check the provided information and click Create.
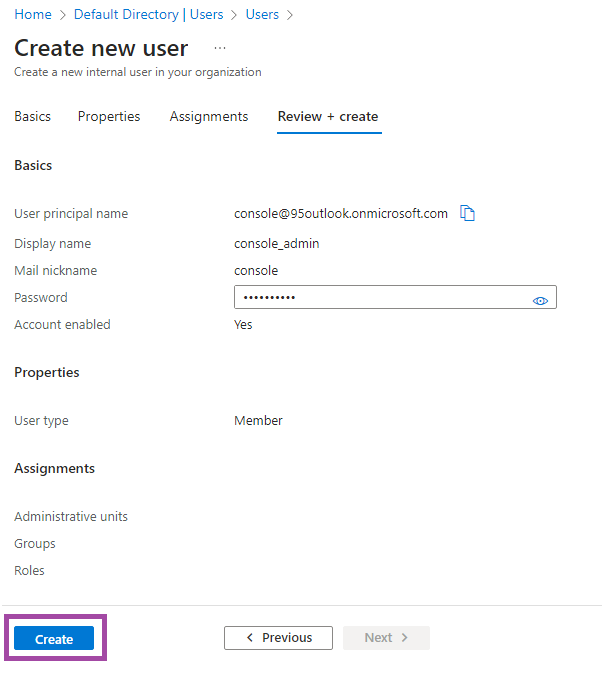
- When the created user appears in the user list, copy the User principal name of this user. You will need this data to create an administrator account in the Management Console.
Grant Required Permissions
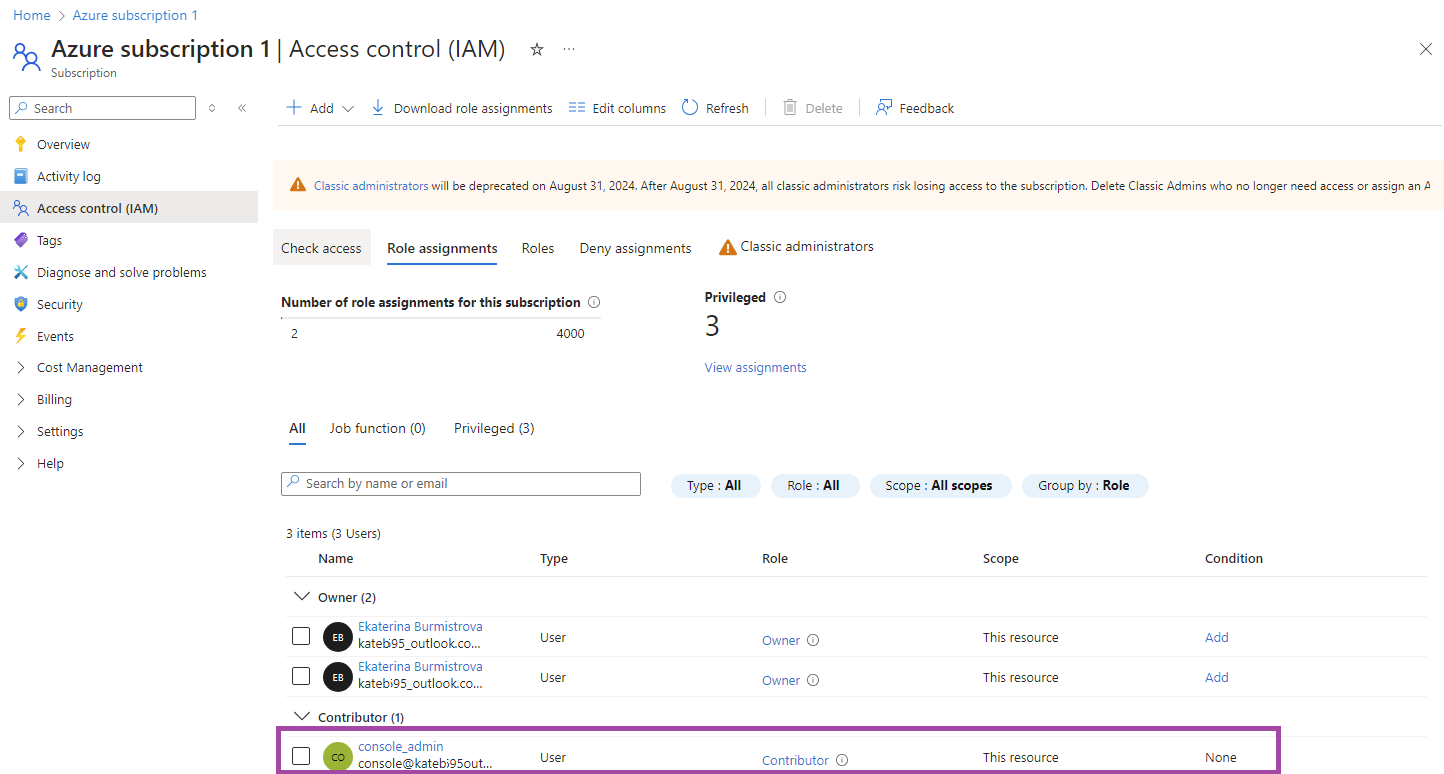
To use the Microsoft Azure Blob storage account and manage the Lifecycle Rules Settings for it, you should grant the newly created user account or an existing account with Owner or Contributor permission to manage your Azure subscription:
- Owner. Users assigned the Owner role have full access to all resources and can manage policies, including creating, editing, and assigning policies.
- Contributor. Users assigned the Contributor role can create and manage all types of Azure resources, including Azure Policy definitions and assignments.
To grant the permission to manage your Azure subscription, perform the following steps:
- Go to the Azure Portal.
- Enter Subscriptions in the top search box to access your subscriptions.
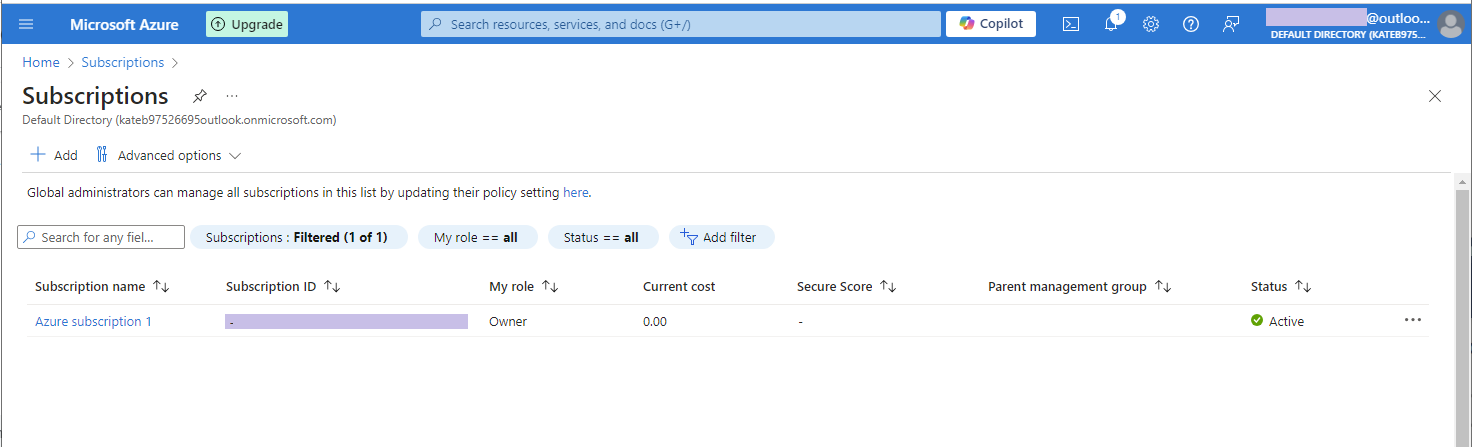
- Click on the required subscription name
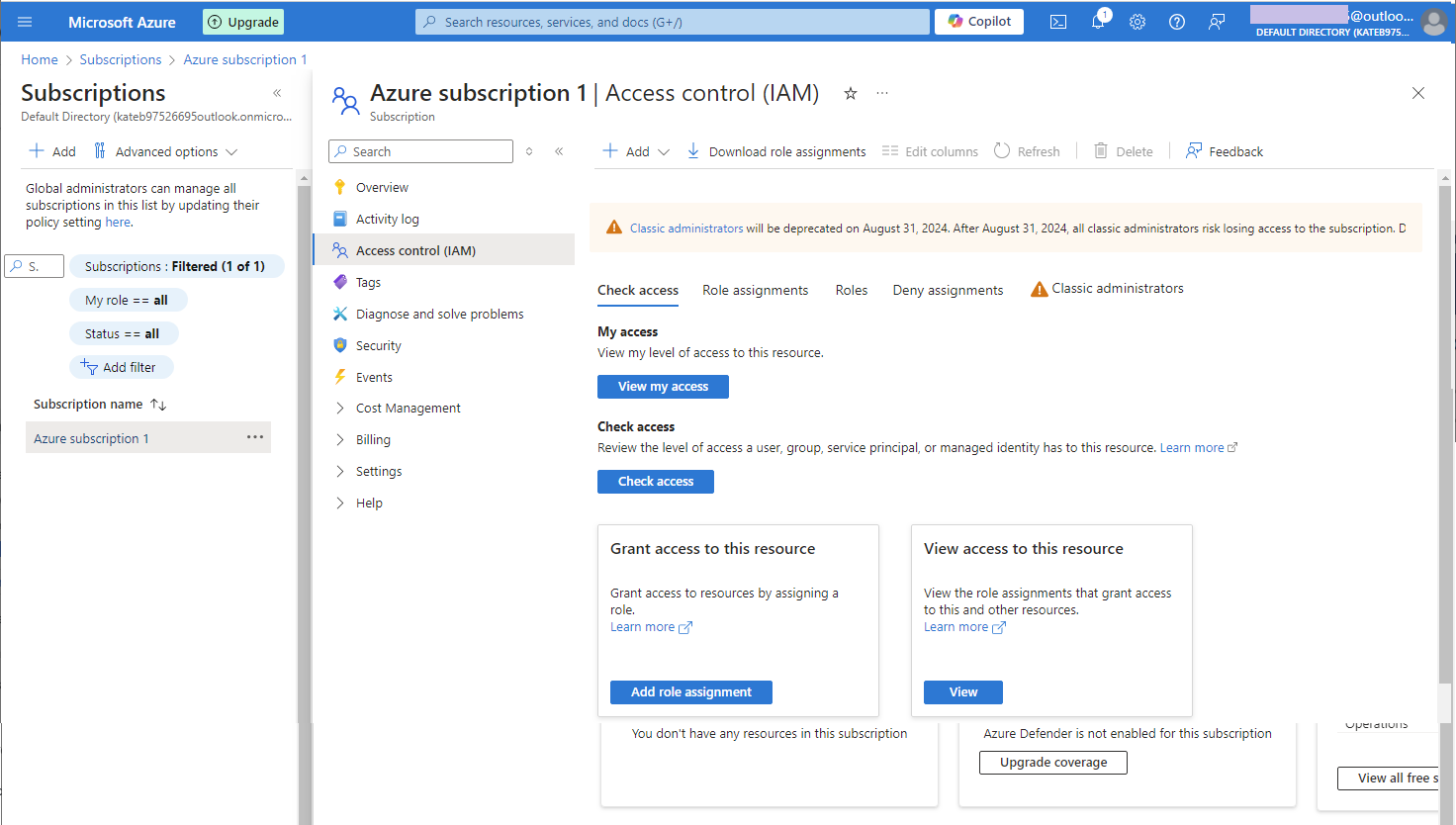
- Click on Access control (IAM) to assign a role to the selected or created account.
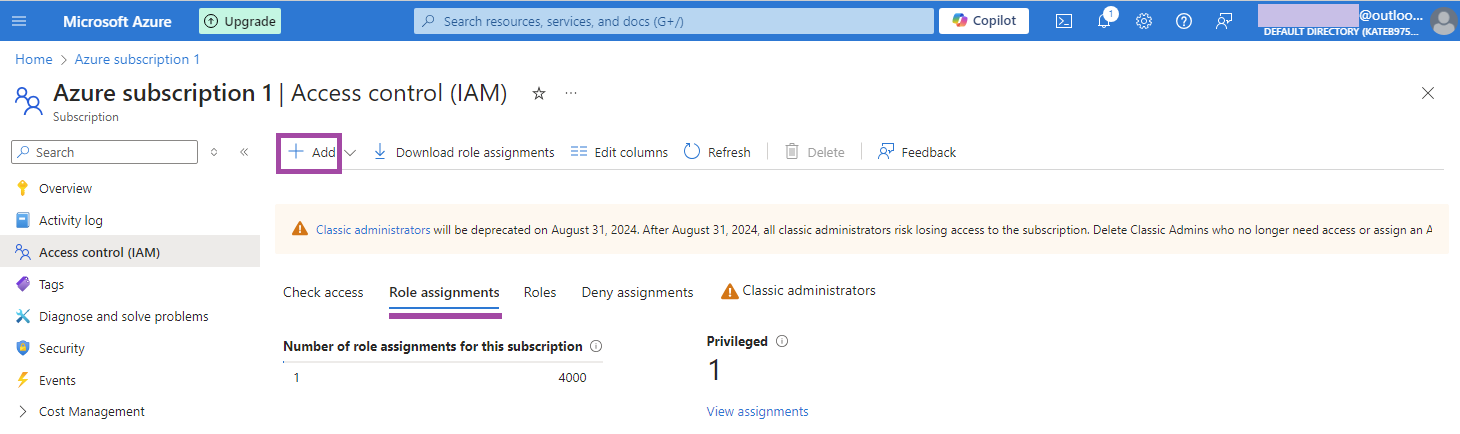
- On the Role Assignment tab, click + Create.
- On the Role tab, select Owner or Contributor role. Search for these roles on Privileged Administrator Roles.
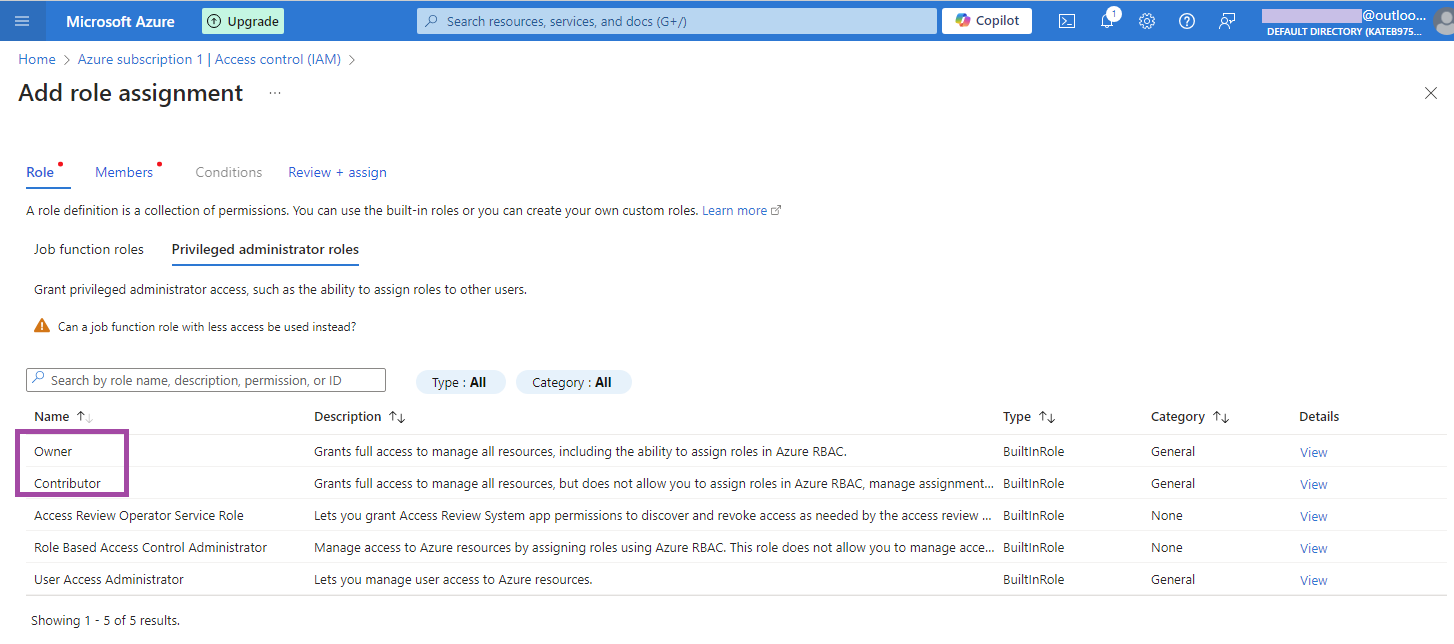
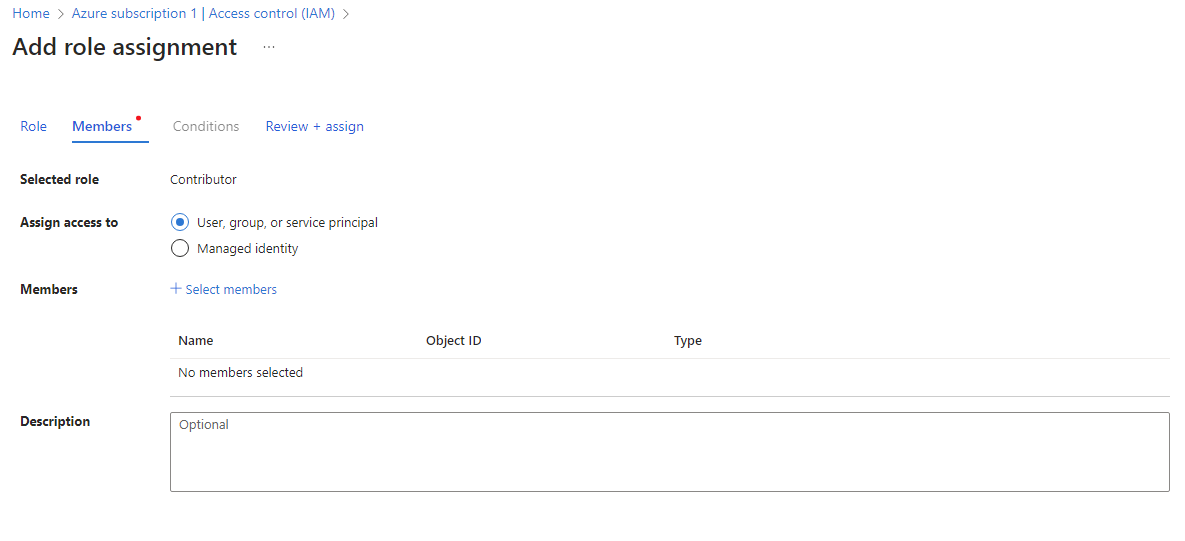
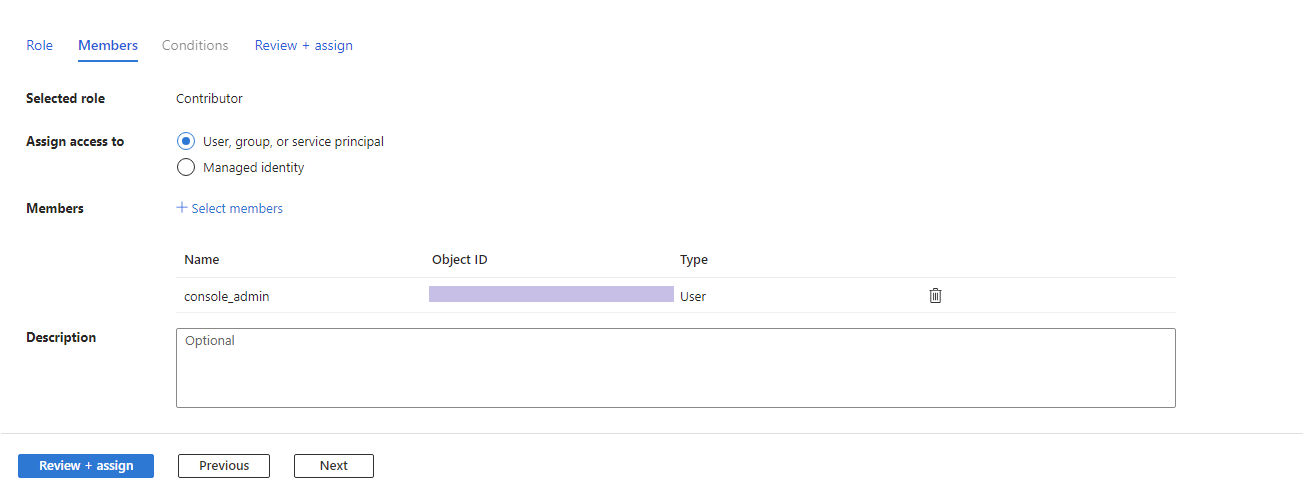
- In this example the Contributor role is selected. On the Members tab, select User, group and service principal radio button, and click + Select members to assign this role to the selected or created account.
- Review and assign the role.
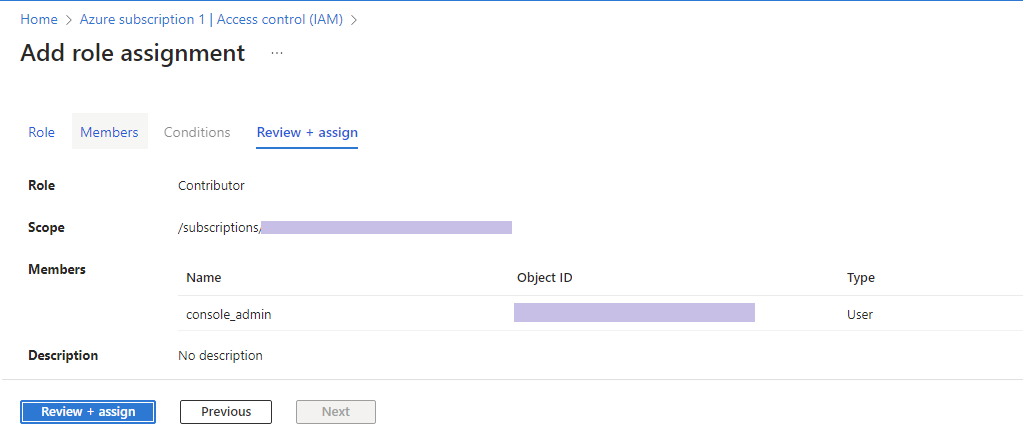
- Once you can see the assigned role on Access control (IAM), you are ready to start using the selected or created account as an administrator to the Managed Backup Service Management Console or for lifecycle policy management.