Add an S3 Account Using IAM Role
This chapter covers the following topic: how to add an Amazon S3 account to Managed Backup using IAM roles.
To start backing up your data, you need to specify cloud storage your data will be backed up to. One of the most popular storage providers is AWS S3. You can add an S3 account in Management Console using the following authentication modes:
- Using the AWS IAM role (recommended). You can use Managed backup wizard or do this manually.
- Using Secret & Access keys (legacy)
However, AWS recommends users use IAM roles for security purposes. IAM roles allow flexible custom settings for available features. Thus, for example, you can create a policy for a user that can back up only to S3 or restore image-based backups to EC2.
To add an S3 account using the IAM role, proceed as follows:
New Storage accounts page To add a new storage account:
- Open the Management Console.
- Open the Backup > Storage Accounts page.
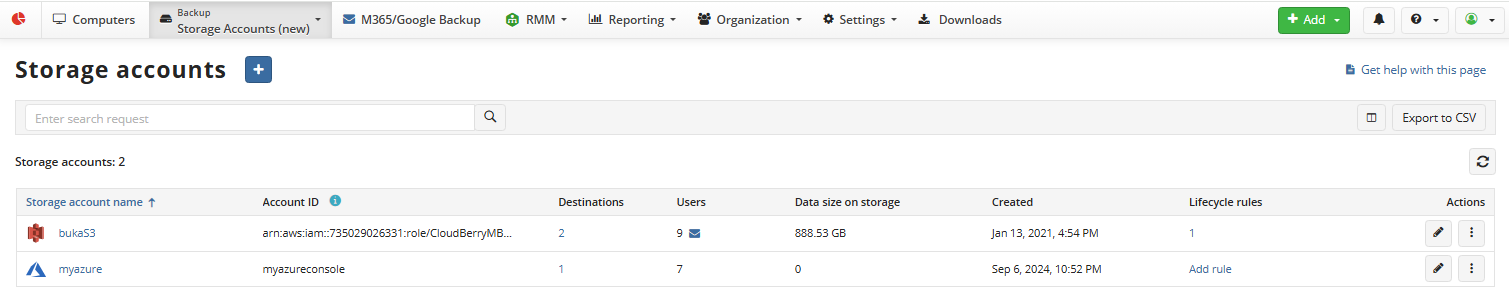
- Click + to launch the Add storage account wizard.
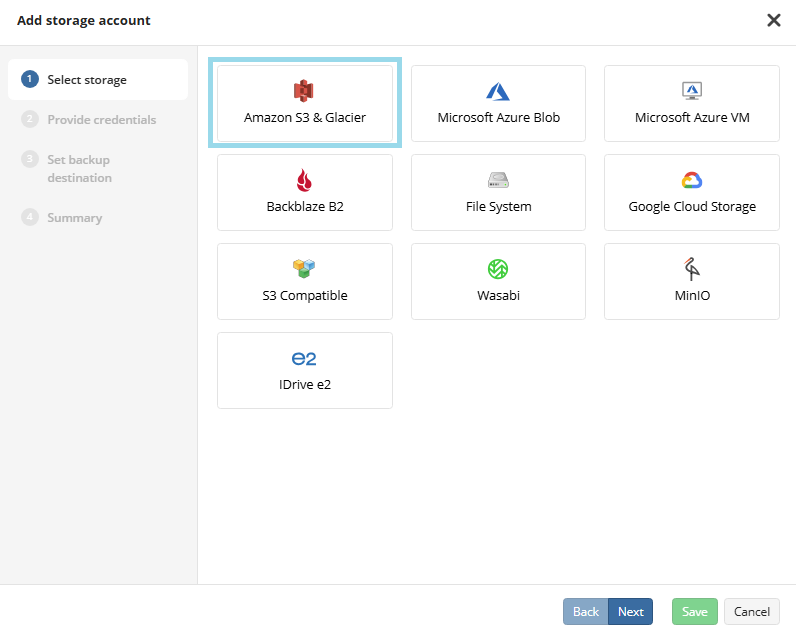
- On the Select storage step select Amazon S3 & Glacier. Click Next.
- On the Provide Credentials step, name the storage account, then select whether you need Amazon S3 & Glacier or Amazon S3 & Glacier (AWS China).
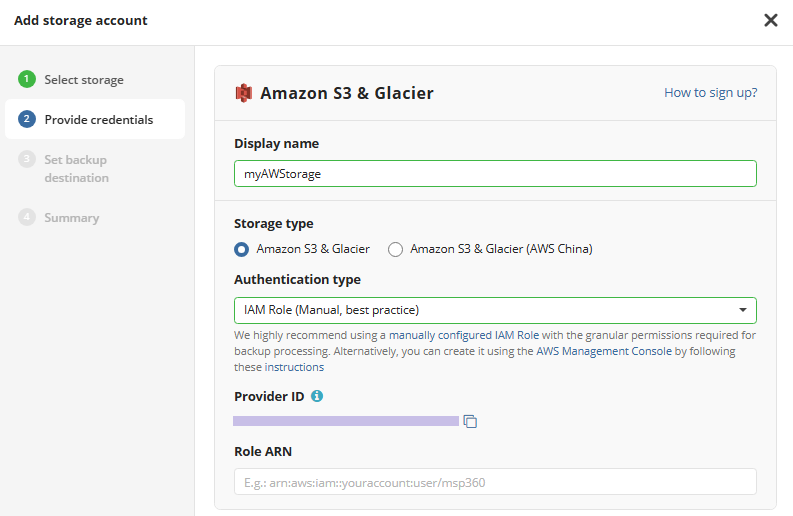
In the Authentication type select IAM Role (Manual, best practice). Also you can select IAM role (MBS wizard) for stepby step instructions.
In the Provider ID field, click the Copy to clipboard icon or copy the Provider ID manually.
Enter Role ARN. Refer to the Add Amazon S3 Account via AWS IAM roles for details.
Click Next. Now you can set the backup destination.
Legacy Storage Accounts page:
- Open the Management Console.
- In the Storage menu, select Storage Accounts.
- Click Add Account.
- Specify the displayed name, then in the Authentication type select IAM Role (Manual, best practice).
- In the Provider ID field, click Copy to clipboard or copy the ID manually.
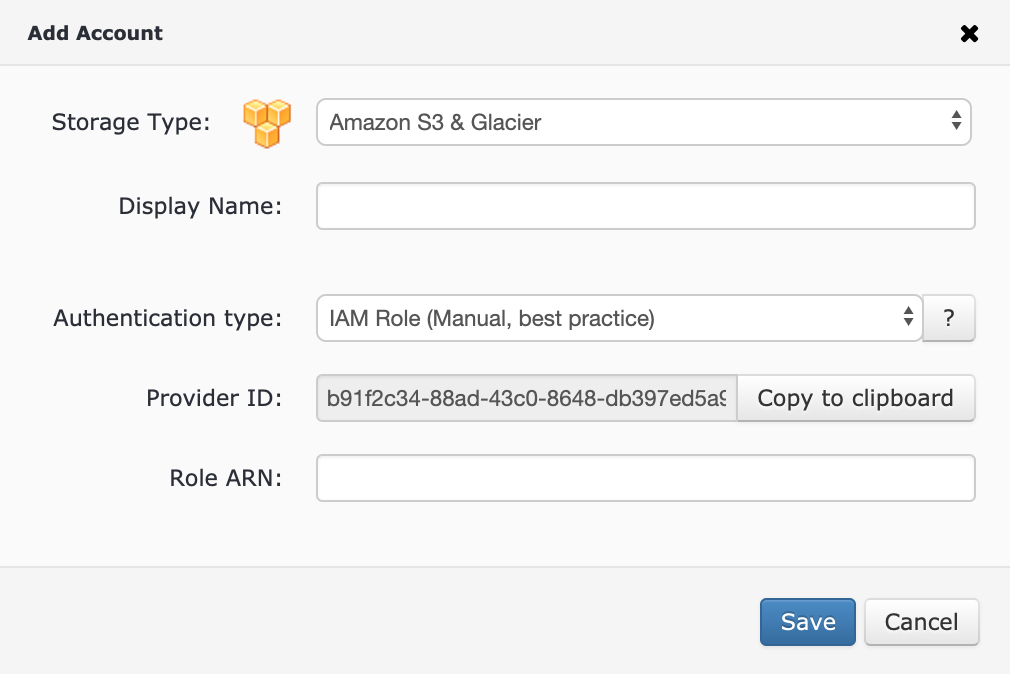
Enter Role ARN. Refer to the Add Amazon S3 Account via AWS IAM roles for details.
Now you can set the backup destination.