Products: Managed Backup (Agent), Managed Backup (Web)
Article ID: m0214Last Modified: 04-Oct-2024
Enable EC2 and EBS Restore Capabilities
The ability to restore EC2 and EBS capabilities depends on the existence of the vmimport service role that has the necessary permissions to perform import operations on your behalf. You need to create this role separately, in addition to following the steps outlined in the 'Add an S3 Account Using IAM Role' article.
- Log in to your Amazon Web Services management console using either root credentials or user credentials with permissions allowing IAM management.
- Use the search box to locate the IAM > Roles section:
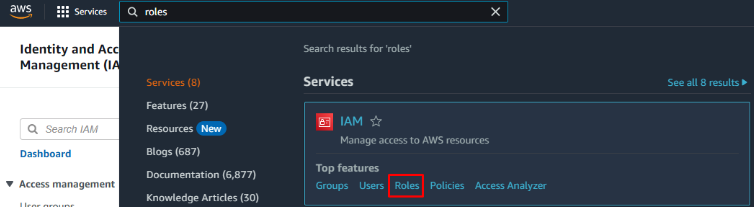
- Click Create role.
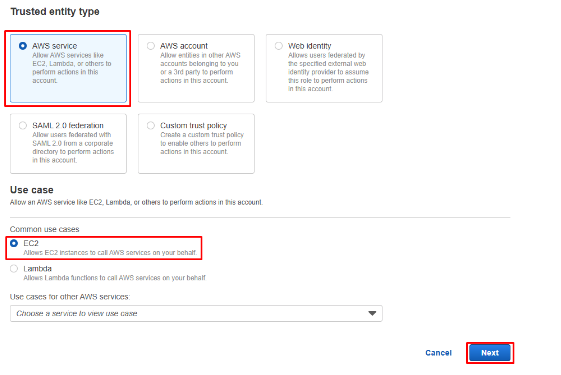
- On Select Trusted Entity area, keep Trusted entity type as AWS service and set Use case to EC2. Click Next.
- On the Add permissions step, click Create policy.
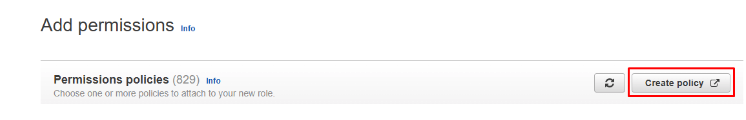
- On Create Policy click JSON tab.
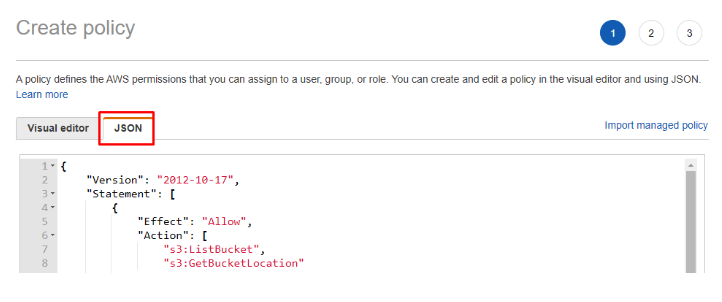
- Paste the code from the snippet:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::*/*"
]
},
{
"Effect": "Allow",
"Action": [
"ec2:ModifySnapshotAttribute",
"ec2:CopySnapshot",
"ec2:RegisterImage",
"ec2:Describe*"
],
"Resource": "*"
}
]
}
- Click Next
- On Tags, add tags, if necessary. Click Next
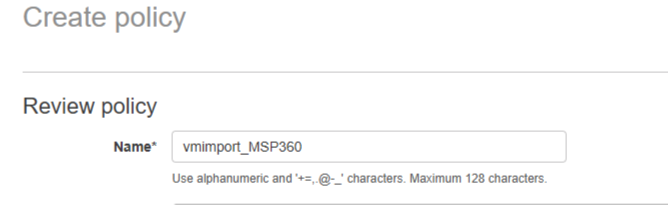
- On Review Policy, name the created policy. Click on Create policy at the bottom of the page.
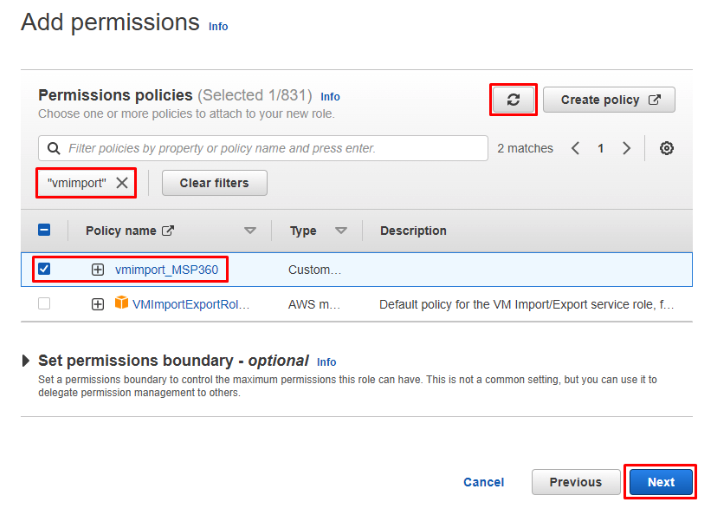
- Go back to the previous browser tab (i.e. containing the page with the Role creation wizard) and refresh the policy list. Find the freshly created policy, select it, and click Next at the bottom of the page.
- Name the role as vmimport, and click on Create role at the bottom of the page:
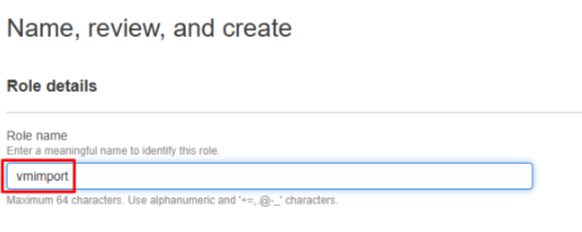
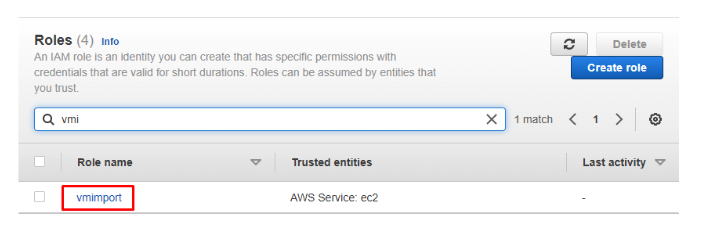
- On the Roles section of the console, check that the created vmimport role appears.
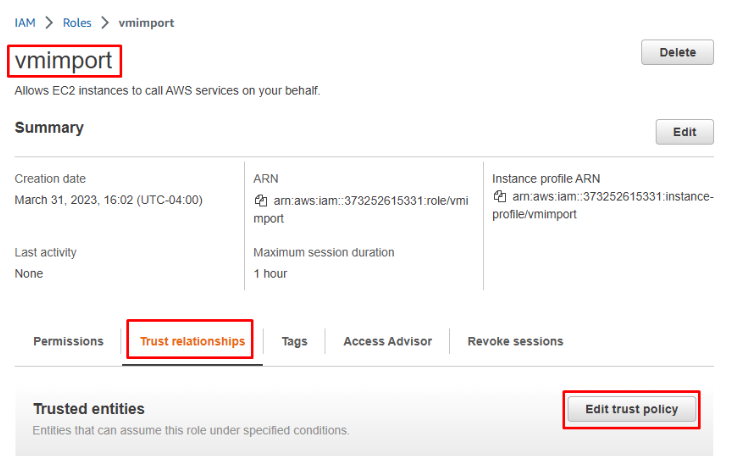
- Click on the role to access parameters.
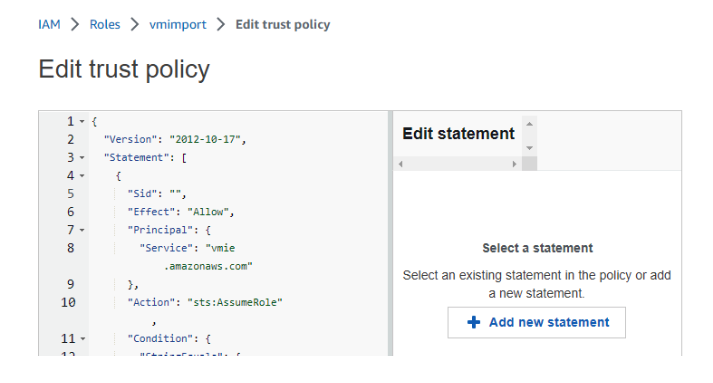
- On parameters page, switch to the Trust relationships tab and click Edit trust policy button:
- Replace the existing JSON code with the following snippet:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Service": "vmie.amazonaws.com"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "vmimport"
}
}
}
]
}
- Click Update policy button at the bottom of the page.